How to use the Nexcess Secure Password Generator to create a secure password or evaluate one.
It is critical that you use a complex, secure password for your Nexcess hosting account. Hackers constantly innovate new ways of stealing data from businesses and individuals. To minimize the risk of a security compromise, regularly change your password for all of your online accounts and use a unique password for each account.
Traditional generator
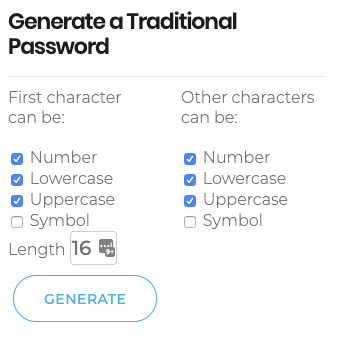
It can be difficult to create and maintain secure passwords, especially when you have several online accounts, each with a unique password. The Nexcess Secure Password Generator can instantly generate a random password to your specifications. For example, if you require a case-sensitive password with only alphanumeric characters, you can select or clear the corresponding check boxes as shown below.
Word-based password generator
The Secure Password Generator utility also provides an option to generate a multi-word password with or without numeric characters.
The How many numbers field refers to how many number pairs will appear within the password.
The How many words field will insert your preferred number of unrelated words in the password. You may also elect to Enter the desired number of words and click Generate.
As shown below, the newly created multi-word password appears on the window under the New Password field. You can then copy and paste the password or save it for future reference.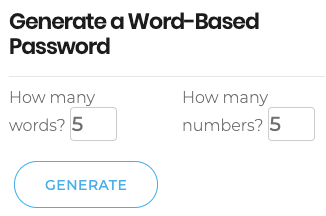
Evaluating passwords
To check the security level of one of your existing passwords, enter the password in the Enter your password field. As you type, the page displays information about the strength of the word: "very weak," "very strong," or something in between.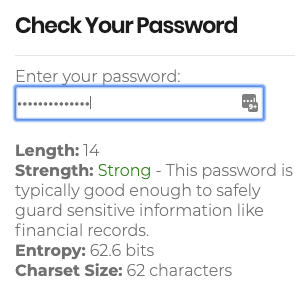
Password managers and two-factor authentication
If maintaining unique, complex passwords for all of your applications sounds difficult, you can use a password-management application like LastPass, Dashlane, or 1Password to safely catalog and encrypt your unique passwords in the cloud under one unique master password.
They also offer two-factor authentication, and we strongly recommend this additional security measure requiring a second form of identity confirmation.
In the event a hacker successfully compromises your password, the hacker still cannot gain access without the second form of authentication. This second form may require a thumb-drive, a fingerprint scanner, or a mobile device.
For 24-hour assistance any day of the year, contact our support team by email or through your Client Portal.